When teams operate independently, it creates communication gaps that can lead to disorder. In contrast, when teams collaborate, they tend to be more efficient.
What is SecOps – The powerful approach that is revolutionizing the process to tackle cybersecurity threats for organizations. Data and data security is the main aspect of any business. However, businesses of all sizes whether it is SMBs or startups face a lot of challenges in keeping their valuable data safe.
In this blog, we will delve into what is SecOps, exploring its key principles, processes, and benefits, and equipping you with the knowledge needed to strengthen your organization’s security posture. So, whether you are an IT professional, a business owner, or simply someone interested in enhancing cybersecurity, this guide will serve as your roadmap to understanding and implementing effective SecOps solutions. Let’s get started;
SecOps or Security operations form the backbone of an organization’s security efforts, keeping all the vital information safe from cyber threats. Highly skilled professionals work tirelessly to protect your digital assets safely, acting as defenders, and constantly monitoring and responding to potential security incidents. In addition, the operations they perform can be carried out either in-house or through a specialized Security Operations Center (SOC) provided by a trusted third party.
Security operations comprise a powerful combination of people, processes, and cutting-edge technology serving as a centralized hub, coordinating all security-related activities within your organization. From threat detection to incident response, security operations keep a vigilant eye on your corporate IT infrastructure, ensuring nothing slips through the cracks.
To accomplish this, security operations rely on a wealth of valuable metrics collected from various devices and data repositories scattered across your network. These collected metrics, harvested by advanced tools and technologies, provide crucial insights into potential security events. They help security professionals detect, interpret, and swiftly resolve any suspicious activities before they can inflict harm.
To simplify it more, I have broken it into some points for better understanding:
When it comes to securing your data or sensitive information within a company, it is essential to understand the respective roles and responsibilities of each stakeholder involved.
Security Operations are important for several reasons:
1 | Advanced Threat Landscape | Quickly respond to bugs & threats by gathering intelligence and staying updated on attack techniques. |
| 2 | Threat Detection and Response | Continuously monitor systems and networks to mitigate threats before they cause significant damage. |
| 3 | Incident Management | Investigate security breaches, determine their impact, and take immediate action to remediate the incidents, minimizing disruptions. |
| 4 | Compliance & Risk Management | Implementing security controls, conducting assessments, and enforcing policies to reduce data breaches and regulatory penalties. |
| 5 | Proactive Security Measures | Take Proactive measures by performing vulnerability assessments and providing security awareness training to employees. |
| 6 | Business Continuity | Contribute to business continuity by protecting critical systems and data from threats to minimize security incidents, and reduce downtime. |
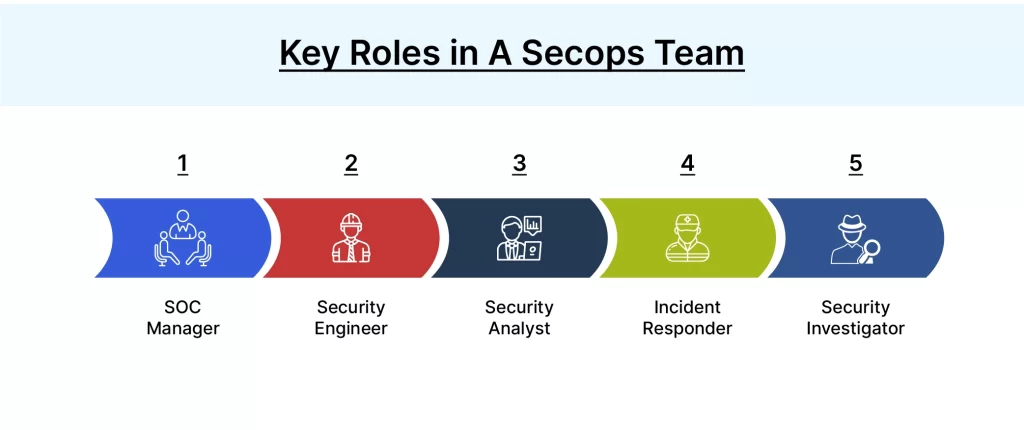
Organizations cannot afford to overlook the importance of Security Operations. By proactively managing risks, detecting threats, and responding effectively, they safeguard sensitive information, maintain customer trust, and mitigate potential financial and reputational damage. It is also crucial to know the key roles in a secops team showed in the below picture.
The integration of security and operations teams that is also called SecOps brings forth numerous advantages for organizations. By breaking down siloes and establishing a dedicated Security Operations Center (SOC), businesses can unlock the following benefits:
SecOps bolsters the security of technology and development environments, ensuring comprehensive protection against evolving threats.
Organizations gain greater visibility into security vulnerabilities, enabling proactive identification and mitigation of risks.
SecOps fosters collaboration among teams, facilitating the swift resolution of security issues through shared expertise and coordinated efforts.
By aligning code changes with deployment rules, SecOps minimizes configuration errors and disruptions to applications, ensuring uninterrupted operations.
SecOps provides valuable insights that inform risk management processes, enabling organizations to build a stronger security posture.
SecOps harmonize security and operations, striking a balance between application security, performance, reliability, and integrity. This leads to improved operational efficiency and reduced downtime.
Implementing a Secops approach in an organization can empower teams to embed security into the development environment from the start, creating products that are largely free from vulnerabilities. It enables the proactive application of security policies, leveraging “policies-as-code” to automatically enforce consistent standards across all IT resources. This proactive stance safeguards the enterprise while fostering innovation.
Furthermore, SecOps facilitates;
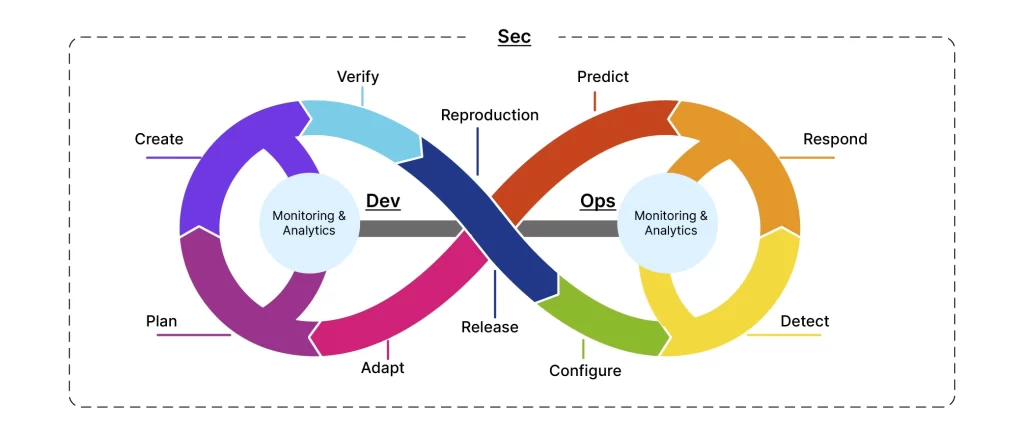
Thus, SecOps brings together the best of security and operations, fortifying organizations against threats, promoting efficiency, and fostering a culture of continuous improvement. In addition, the relationship between DevOps and Secops is also important, let’s overview first what is devsecops;
DevSecOps and SecOps are two approaches that emphasize the integration of security practices into software development and operational processes. While they share a common goal of enhancing security, there are distinct differences between the two:
DevSecOps, short for Development Security Operations, is an approach that emphasizes the integration of security practices and principles into the software development process. It aims to bridge the gap between development, operations, and security teams by fostering collaboration and implementing security measures throughout the entire software development lifecycle.
In traditional software development, security is often treated as a separate concern, addressed only towards the end of the development cycle. However, DevSecOps promotes a “shift-left” mentality, where security is integrated early on, starting from the design and development phases. By embedding security into every stage of the development process, organizations can identify and address vulnerabilities and potential threats at an early stage, reducing the risk of security breaches later on.
In addition, DevSecOps encourages a proactive and continuous approach to security, leveraging automation, and implementing security controls as code. It promotes the use of security testing, vulnerability scanning, and compliance checks throughout the development pipeline, ensuring that security is built into the application from the ground up.
Organizations can create a security-focused culture, where security considerations are integrated throughout the development process resulting in more secure, reliable, and resilient applications and enhancing the overall security posture of the organization.
DevSecOps | SecOps |
|---|---|
DevSecOps is embedding security throughout the entire software development lifecycle. The goal is to build a security culture where security is everyone’s responsibility, and secure applications are delivered more efficiently and rapidly. | SecOps, or Security Operations, focuses on the coordination and management of security within an organization’s operational environment. It involves monitoring, detecting, and responding to security incidents in real-time. |
Let’s explore some key features of DevSecOps and SecOps:
Key Features ofDevSecOps | Key Features ofSecOps |
|---|---|
1. Shift-left mentality: Security is addressed from the beginning, with security considerations incorporated into the development process, code reviews, and testing. | 1. Incident response: Security Operations teams are always responsible for monitoring as well as responding to security incidents that happen promptly, minimizing the impact of breaches. |
2. Automation: DevSecOps relies heavily on automation to enable continuous security testing, vulnerability scanning, and compliance checks. | 2. Security controls: SecOps involves implementing and maintaining security controls, conducting vulnerability assessments, and ensuring compliance with regulations. |
3. Collaboration: DevSecOps promotes collaboration between development, operations, and security teams to ensure seamless integration of security controls and practices. | 3. Collaboration: Security Operations is an agile approach that promotes collaboration between security teams and operations teams to effectively address vulnerability and security threats. |
To conclude, we can say that while DevSecOps focuses on integrating security practices throughout the development process, SecOps primarily concentrates on the operational aspects of security incident management and vulnerability mitigation. Both approaches play vital roles in ensuring comprehensive security, and organizations often adopt a combination of DevSecOps and SecOps to achieve a holistic and robust security posture. IntellicoWorks provides SecOps services that aim to create a secure and resilient environment by aligning security principles, processes, and technologies across the organization.
Follow IntellicoWorks on LinkedIn for more insights!

Talk to us and let’s build something great together
A Subsidiary of Vaival Technologies, LLC
IntelliCoworks is a leading DevOps, SecOps and DataOps service provider and specializes in delivering tailored solutions using the latest technologies to serve various industries. Our DevOps engineers help companies with the endless process of securing both data and operations.
Ops
Cloud
AI & ML
Copyrights © 2023 byIntellicoworks. All rights reserved.