When teams operate independently, it creates communication gaps that can lead to disorder. In contrast, when teams collaborate, they tend to be more efficient.
In today’s technological landscape, the DevOps approach has revolutionized software development and deployment. Using DevOps services can increase agility and efficiency and also enable organizations to deliver applications at a rapid pace. However, the integration of security measures into the DevOps pipeline is vital to protect against cyber threats and safeguard sensitive data.
This article aims to provide insights into best practices for securing your DevOps pipeline against potential risks and ensuring the safety of your software applications.
A set of interconnected tools, processes, and practices that facilitate the continuous integration, delivery, and deployment of software applications. Although, it encompasses the entire software development lifecycle, from code development to production deployment.
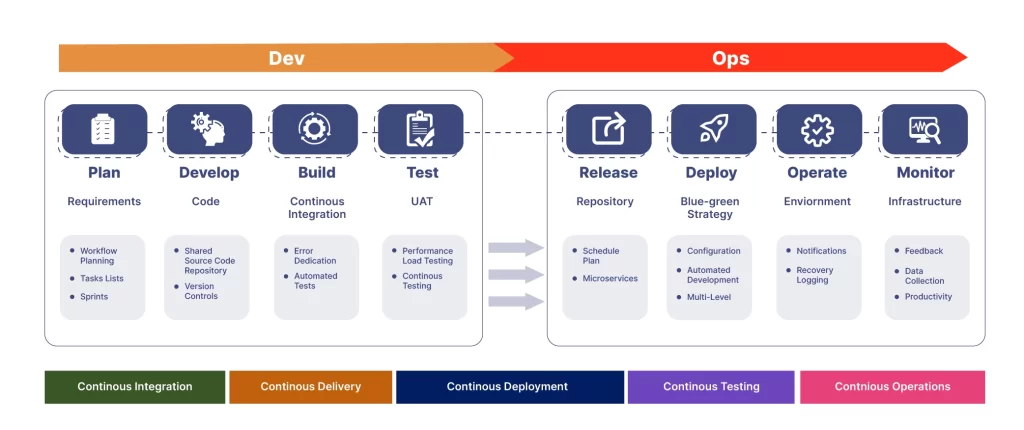
As you can see in the image below, each stage is automated and connected to the subsequent stage, ensuring a seamless flow of code changes through the pipeline. Continuous integration and continuous delivery (CI/CD) practices are central to a DevOps pipeline, enabling frequent code integration, automated testing, and rapid deployment.
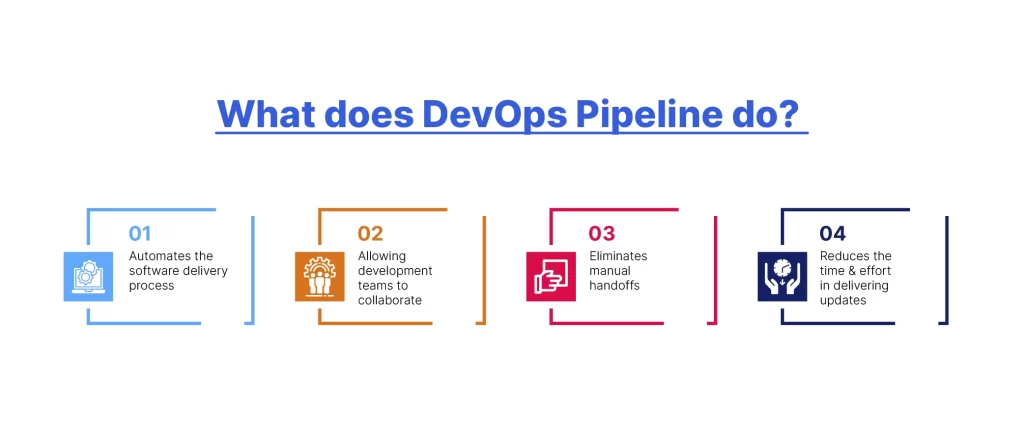
By implementing a DevOps pipeline, organizations can achieve:
DevOps security plays an important role in mitigating risks associated with the software development and deployment process. Although, if you ignore DevOps security, it can lead to severe consequences, such as;
By integrating security measures from the inception of the DevOps pipeline, organizations can proactively identify and address vulnerabilities, ensuring the integrity and confidentiality of their applications and data.
Real-life examples of cyber threats in the DevOps pipeline further illustrate the pressing need for DevOps security practices.
An approach to embed security measures into every phase of the software development lifecycle.
By incorporating security from the initial design stage, organizations can build resilient and secure applications. Implementing Security by Design in the DevOps pipeline involves thorough threat modeling, risk assessments, and secure architecture design. As a result, this ensures security considerations are an integral part of the development process, minimizing vulnerabilities and enhancing the overall security posture.
A practice involving ongoing monitoring, testing, and remediation of security vulnerabilities throughout the DevOps pipeline.
By employing automated security testing tools and techniques, organizations can proactively identify and address potential risks. As a result, continuous security integrates security as an inherent part of the DevOps lines, enabling timely identification and resolution of vulnerabilities.
Secure coding practices are essential for building robust and resilient applications. By adhering to secure coding guidelines and best practices, developers can minimize the risk of introducing vulnerabilities into the software.
In addition, secure coding practices in the DevOps pipeline involve regular code reviews, adherence to secure coding standards, input validation, and output encoding.
As a result, these practices significantly reduce the surface area for potential cyber-attacks.
Configuration management ensures that the software components within the DevOps pipeline are appropriately configured and maintained. By implementing secure configuration management practices, organizations can prevent misconfigurations that may lead to security breaches. Furthermore, it includes implementing least privilege access controls, secure system configurations, and regular patch management.
DevSecOps refers to an evolution of the DevOps approach. In this approach, security is integrated throughout the software development and deployment lifecycle.
Additionally, DevSecOps emphasizes a culture of shared responsibility, collaboration, and automation between development, operations, and security teams.
By adopting DevSecOps practices, organizations can ensure that security is an integral part of the DevOps pipeline, rather than an afterthought.
Threat modeling is a practice that involves identifying potential threats and vulnerabilities in the software system. By analyzing potential attack vectors and assessing their impact, organizations can prioritize security measures based on the level of risk.
Ultimately, incorporating threat modeling in the DevSecOps pipeline allows for proactive security measures, ensuring that potential vulnerabilities are addressed early in the development process.
Vulnerability scanning involves the use of automated tools to scan the DevOps pipeline and identify any known vulnerabilities in the software components. By conducting regular vulnerability scans, organizations can detect and patch security flaws before they are exploited by malicious actors. In addition, this practice enhances the overall security of the DevOps pipeline and reduces the likelihood of successful cyber attacks.
Penetration testing, also known as ethical hacking, simulates real-world cyber-attacks to assess the security of the DevOps pipeline. By conducting controlled and authorized attacks, organizations can identify weaknesses and validate the effectiveness of their security controls. Ultimately, Penetration testing helps uncover vulnerabilities that may go undetected through other security measures and allows for targeted remediation actions.

To conclude we can say that by demonstrating the above fact makes it clear that prioritizing security in DevOps Pipeline is significant. Although, securing your DevOps pipeline against cyber threats is of utmost importance in today’s digital landscape. In addition, By implementing DevOps security practices, such as Security by Design, Continuous Security, Secure Coding Practices, and Configuration Management, organizations can mitigate risks and protect their applications and data. Additionally, adopting DevSecOps practices, including Threat Modeling, Vulnerability Scanning, and Penetration Testing, enhances the overall security posture of the DevOps pipeline. Lastly, securing the DevOps pipeline is a continuous process that requires ongoing monitoring and improvement. So, take the necessary steps to secure your DevOps pipeline against cyber threats and ensure the safety of your applications and data.
IntellicoWorks is a leading provider of DevOps, SecOps, and DataOps solutions. Our expertise lies in streamlining and automating manual and tedious processes to empower organizations with efficient and secure software development and deployment practices. With our comprehensive suite of services, we help businesses enhance their DevOps pipeline and strengthen their security measures.
Follow IntellicoWorks for more insights!

Talk to us and let’s build something great together
A Subsidiary of Vaival Technologies, LLC
IntelliCoworks is a leading DevOps, SecOps and DataOps service provider and specializes in delivering tailored solutions using the latest technologies to serve various industries. Our DevOps engineers help companies with the endless process of securing both data and operations.
Ops
Cloud
AI & ML
Copyrights © 2023 byIntellicoworks. All rights reserved.